
Google Search Tips You Want To Know Now
Discover a wealth of Google tech tips in this EasyIT video! Enhance your online search experience with techniques like precise phrase searching and reverse image[...]

Linkedin QRCode Pro Networking Tip
Discover how LinkedIn's QR Code feature can revolutionize your networking experience. Streamline connections, share profiles effortlessly, and navigate events with ease. Unlock the power of[...]

A Clean Inbox Is A Happy Inbox
Discover expert Microsoft Outlook tips to achieve a clutter-free inbox and boost productivity with EasyIT Clean Inbox. Say goodbye to email overwhelm and hello to[...]

Splitwise: A Great Tool To Help Split Expenses With Friends
Discover how Splitwise simplifies splitting bills with friends! EasyIT's guide to this user-friendly app ensures you manage shared expenses effortlessly. Say goodbye to money hassles[...]

OpenTable Helps You Stay In The Good Books This Valentine’s Day
Discover how to effortlessly reserve the perfect Valentine's dinner with EasyIT's step-by-step guide on using OpenTable. Secure your romantic evening hassle-free!
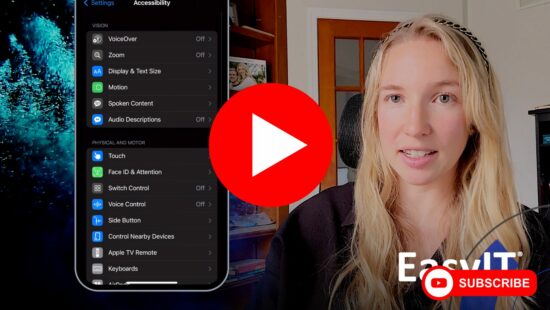
How To Enable LED Flash Notifications On Your iPhone
Enable LED flash notifications on your iPhone easily with EasyIT. Never miss crucial alerts – follow our simple guide for a customized and upgraded iPhone[...]

Huge Google Chrome Time Saver
Unlock the full potential of your browsing experience with EasyIT's Google Chrome Time Saver extension. Navigate effortlessly through tabs and web pages using the innovative[...]

25+ Years Supporting Willie Neumann Save Columbus Organizations
Whenever Willie needs help solving a problem or handling damage control, he knows he can call EasyIT. That’s why we’ve worked together for nearly three[...]

Having Fun With Stickers And iPhone Photos
Explore a world of creativity with iPhone stickers on EasyIT Monday with Megan! Join Megan as she shares fun and easy ways to personalize your[...]
