
Cybercrime and Security for SMBs
Did you know the illicit trading of personal data was worth $3.88 billion last year? Cybercrime is a growing industry known for its innovation. It[...]

SMBs: It Is Hackers v. You – Don’t Let Them Score
SMBs: It Is Hackers v. You – Don’t Let Them Score Selling stolen IDs and other personal data is a lucrative trade for hackers. They[...]

BYOD: Why is This Concept So Attractive to Employees?
BYOD: Why is This Concept So Attractive to Employees? Bring Your Own Device, or BYOD, to work was an idea a few years ago that[...]

The Most Boring Topic Ever – Phone Systems
Yes, today’s blog is about office phone systems. You have one. They are dull, necessary, and no one wants to deal with them. They need[...]
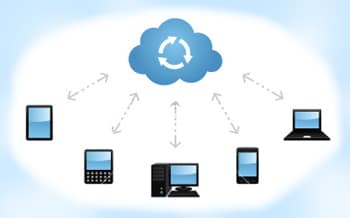
Benefits of Using VoIP Technology
Benefits of Using VoIP Technology More and more businesses are implementing Voice over Internet Protocol or VoIP technology because of its versatility, flexibility and cost[...]

Data Breaches are a Question of When, Not If
You hear on the news all of the time about big cyber attacks on large corporations, and even government agencies. The trouble with this news[...]

What is Ransomware and How Can it Affect Your Business?
This cyberattack scheme hasn’t garnered nearly as much attention as the usual “break-in-and-steal-data-to-sell-on-the-Internet version,” but it can be even more debilitating. Ransomware attacks have begun[...]

Data Security: A People Problem
There are some things that only people can fix. There are many security risks to your data, but there is one method that remains a[...]

IT Defense In Depth Part I
In the 1930s, France built a trench network called the Maginot Line to rebuff any invasion. The philosophy was simple: if you map out all[...]
